Adding a New Validator to an Existing Setup with Existing Seed Words
Scenario: Genesis block is long passed and now you would like to add more validators with your existing mnemonic seed.
✅ Requirements
Before continuing please have the following ready:
Existing 24 word validator mnemonic phrase
Existing keystore password
ETH Withdrawal Address from your hardware wallet
Optional Step 0: Cleanup leftover validator_keys
Verify that you have backups of validator_keys directory. The contents are the keystore files.
Having backup copies of your validator_keys directory on USB media can make recovery from node problems quicker. Validator keys can always be regenerated from secret recovery mnemonic phrase.
You may safely delete the directory.
# Remove default validator_key directory
sudo rm -r $HOME/staking-deposit-cli/validator_keysStep 1: Create new deposit_data json file and new validator_keys
In this example, using the staking-deposit-cli tool, you can add more validators by creating a new deposit data file and validator_keys
Security recommendation reminder: For best security practices, key management and other activities where you type your 24 word mnemonic seed should be completed on an air-gapped offline cold machine booted from USB drive.
Reminder to use the same keystore password as existing validators.
For example, in case we originally created 3 validators but now wish to add 5 more validators, we could use the following command.
--validator_start_index
Number of validators you ALREADY created
--num_validators
Number of NEW validators you want to create
--chain
Options: mainnet holesky goerli
--execution_address
Critically important: Your Ethereum Address from a Hardware Wallet.
Withdrawals will be sent to this address. If you stop validating and exit your validator, your 32 ETH will be sent here.
This ETH withdrawal address is one such that you control the private keys to, ideally one from a hardware wallet.
🛑DO NOT USE A EXCHANGE ADDRESS!🛑
Step 2: Deposit 32 ETH per validator
Option 1: Visit the official Ethereum Launchpad site
Two important tasks to complete at the launchpad.
Upload the
deposit_data-#########.jsonMake the 32 ETH deposit transaction(s), 32 ETH per validator. 1 deposit transaction per validator.
Option 2: Use Abyss's Batch Ethereum Depositor to combine many validator deposits into just 1 transaction.
Step 3: Import New Validator Keys
This step assumes your new validator keys are located in
If Wagyu was used to generate validator keys, move the keystore files to the above location.
Stop your validator client.
Import your validator keys by importing your keystore file. Be sure to enter your keystore password correctly.
Verify that your keystore file was imported successfully.
Once successful, you will be shown your validator's public key.
For example, 0x8d9138fcf5676e2031dc4eae30a2c92e3306903eeec83ca83f4f851afbd4cb3b33f710e6f4ac516b4598697b30b04302
Setup ownership permissions, including hardening the access to this directory.
Finally, start your validator client.
Check your logs to confirm that the validator clients are up and functioning.
For example when using 2 validators, logs will show the following:
Stop your validator client.
Import your validator keys by importing your keystore file. Be sure to enter your keystore password correctly.
Verify that your keystore file was imported successfully.
Once successful, you will be shown your validator's public key.
For example, 0x8d9138fcf5676e2031dc4eae30a2c92e3306903eeec83ca83f4f851afbd4cb3b33f710e6f4ac516b4598697b30b04302
Setup ownership permissions, including hardening the access to this directory.
Finally, restart to use the new validators.
Check your logs to confirm that the validator clients are up and functioning.
For example when using 2 validators, logs will show the following:
Press Ctrl + C to exit the logs.
Option 1: For standalone validator
Stop your Teku client.
Storing your keystore password in a text file is required so that Teku can decrypt and load your validators automatically.
Create a temporary file to store your keystore password. Type your password in this file.
To exit and save, press Ctrl + X, then Y, then Enter.
Confirm that your keystore password is correct.
Run the following command to create a corresponding password file for every one of your validators.
Copy keystores to validator folder
Setup ownership permissions, including hardening the access to this directory.
Verify that your validator's keystore .json files and validator's passwords .txt files are present by checking the following directory.
Example output of two validator's keystore.json files with matching password.txt files.
Delete the temporary keystore password file.
Finally, restart Teku to use the new validators.
Check your logs to confirm that the validators are up and functioning.
For example when using 2 validators, logs will show the following:
Option 2: For Combined CL+VC
Stop your Teku client.
Storing your keystore password in a text file is required so that Teku can decrypt and load your validators automatically.
Create a temporary file to store your keystore password. Type your password in this file.
To exit and save, press Ctrl + X, then Y, then Enter.
Confirm that your keystore password is correct.
Run the following command to create a corresponding password file for every one of your validators.
Copy keystores to validator folder
Setup ownership permissions, including hardening the access to this directory.
Verify that your validator's keystore .json files and validator's passwords .txt files are present by checking the following directory.
Example output of two validator's keystore.json files with matching password.txt files.
Delete the temporary keystore password file.
Finally, restart Teku to use the new validators.
Check your logs to confirm that the validators are up and functioning.
For example when using 2 validators, logs will show the following:
Option 1: For standalone validator
Stop your Nimbus client.
Enter your keystore password to import accounts.
Now you can verify the accounts were imported successfully by doing a directory listing.
You should see a folder named for each of your validator's pubkey.
Setup ownership permissions, including hardening the access to this directory.
Finally, restart Nimbus to use the new validators.
Check your logs to confirm that the validators are up and functioning.
For example when using 2 validators, logs will show the following:
Option 2: For Combined CL+VC
Stop your Nimbus client.
Enter your keystore password to import accounts.
Now you can verify the accounts were imported successfully by doing a directory listing.
You should see a folder named for each of your validator's pubkey.
Setup ownership permissions, including hardening the access to this directory.
Finally, restart Nimbus to use the new validators.
Check your logs to confirm that the validators are up and functioning.
For example when using 2 validators, logs will show the following:
Stop your validator client.
Import your validator keys by importing your keystore file. When asked to create a new wallet password, enter your keystore password. When prompted for the imported accounts password, enter your keystore password again.
If using Binaries,
If Built from Source,
Verify that your keystore file was imported successfully.
If using Binaries,
If Built from Source,
Once successful, you will be shown your validator's public key. For example:
Setup ownership permissions, including hardening the access to this directory.
Finally, restart Prsym validator to use the new validators.
Check your logs to confirm that the validator clients are up and functioning.
For example when using 2 validators, logs will show the following:
Step 4: Backup and Delete validator_keys directory
validator_keys directoryMake backup copies of your validator_keys directory to USB media or other devices. These validator keys can always be regenerated from secret recovery mnemonic phrase.
Afterwards, you may safely delete the directory.
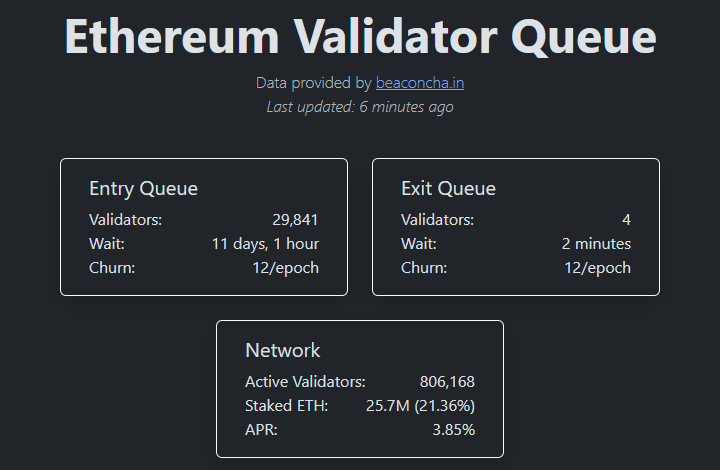
Step 5: Estimate when your new validator becomes active
Your additional validators are now in the activation queue waiting their turn. Check the "Entry Queue" for your estimated wait time at https://www.validatorqueue.com
In the below example, the wait time was approximately 11 days, 1 hour until a new validator became active.